- June 30, 2015
- Posted by: Surender Kumar
- Category: Cisco Routers
Network Address Translation (NAT)
Table of Contents
Network Address Translation is a process in which private IP addresses (non-routable) are translated or mapped into public IP addresses (routable).
This is very important concept because every device need a public IP address in order to connect to internet and due to increased popularity of internet caused the whole IP address space provided by IPv4 to be depleted. This forced the IP designers to create a newer generation of IP which is known as IPv6.
The whole IPv4 address space would have been exhausted very long time ago without Network Address Translation.
You can use NAT if:
- You need to connect to the Internet and your hosts do not have unique public IP addresses.
- You change to a new ISP that requires you to reassign IPs into your network.
- You need to merge two intranets with duplicate addresses.
Advantages of NAT:
- Main advantage is that you can connect unlimited number of devices to internet by purchasing single public IP from ISP.
- It provides an additional layer of security by because original source and destination IP addresses are hidden.
- NAT allows you to prevent renumbering of network in case of company merging with overlapping subnets.
- NAT prevents the fast exhaustion of IPv4 address space.
Disadvantages of NAT:
- The NAT configuration is resource intensive. Means NAT increases the CPU cycles and memory usage on your routers.
- NAT imposes some delay due to time taken in translation process but this delay is negligible.
- NAT causes loss in end to end IP trace capability.
- Certain applications will not function with NAT enabled.
NAT Terminology
- Inside: The term inside refers to the private network owned by an organization or individual.
- Outside: The term outside refers to the public network, most often the Internet, to which the private network connects.
- Global Address: Global address is a public IP address which is routable by internet routers.
- Local Address: Local address is private address as per RFC 1918 which are not routable over internet. These addresses are reserved to be used in LANs.
- Inside Local Address: Inside local address is the name of inside source address before translation process.
- Inside Global Address: Inside global address is the name of inside host after translation.
- Outside Local Address: Outside local address is the name of destination host after translation.
- Outside Global Address: Outside global address is the name of outside destination host before translation.
Types of NAT
- Static Network Address Translation
- Dynamic Network Address Translation
- Port Address Translation (overloading)
1. Static NAT
Static NAT allows the one-to-one mapping between local and global addresses. To configure static NAT, you should have equal number of public IP addresses as the number of hosts in inside network.
2. Dynamic NAT
Dynamic NAT gives you the ability to map a local (private) IP address to a public IP address from out of a pool of public IP addresses. Router will automatically decide which private IP should be mapped to which public IP from pool.
3. Port Address Translation (Overloading)
Port Address Translation or PAT permits multiple devices on a local area network (LAN) to be mapped to a single public IP address. This is done by using different source ports. PAT is the real reason we have not run out of public IPv4 address space so early.
Static NAT Configuration
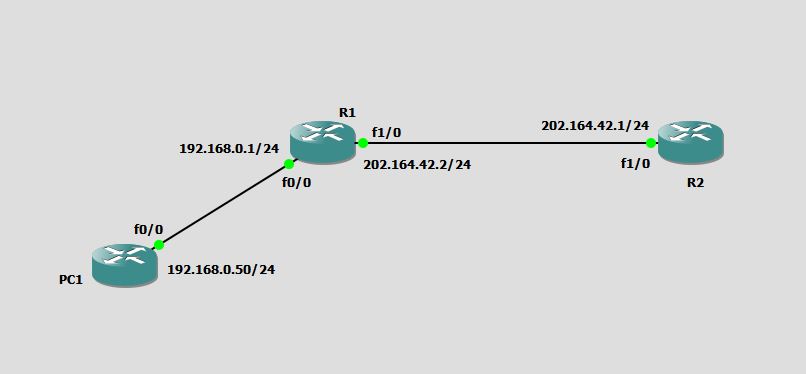
I am going to use this simple network for demonstrating Static NAT configuration.
In above diagram, Consider R1 as a gateway router. So, we will configure NAT on R1.
Now let’s get started.
Configure R1:
R1#config term R1(config)#int fa0/0 R1(config-if)#ip address 192.168.0.1 255.255.255.0 R1(config-if)#no shut R1(config-if)#ip nat inside R1(config-if)#int fa1/0 R1(config-if)#ip address 202.164.42.2 255.255.255.0 R1(config-if)#no shutdown R1(config-if)#ip nat outside R1(config-if)#exit R1(config)#ip nat inside source static 192.168.0.50 202.164.42.50 R1(config)#^Z R1# *Jul 1 17:23:42.767: %SYS-5-CONFIG_I: Configured from console by console R1#
The ip nat inside command is used because interface FastEthernet0/0 is connected to inside network and ip nat outside command is run because interface FastEthernet01/0 is connected to outside network.
The ip nat inside source static 192.168.0.50 202.164.42.50 command is actually telling the router to do the static mapping of source private IP address 192.168.0.50 to public address 202.164.42.50.
Configure R2:
R2#conf t Enter configuration commands, one per line. End with CNTL/Z. R2(config)#int fa1/0 R2(config-if)#ip address 202.164.42.1 255.255.255.0 R2(config-if)#no shutdown R2(config-if)#^Z R2#
There s nothing interesting in R2’s configuration. I have just configured IP address on interface.
Before, I actually show you static NAT in action, I just wanted to tell you that I have not configured any route on R1 to reach R2. have a look at routing table.
R1#show ip route
[output cut]
Gateway of last resort is not set
C 192.168.0.0/24 is directly connected, FastEthernet0/0
C 202.164.42.0/24 is directly connected, FastEthernet1/0
R1#
Now I will move to PC1 and run a ping to R2’s address 202.164.42.1
PC1#ping 202.164.42.1 repeat 20 Type escape sequence to abort. Sending 20, 100-byte ICMP Echos to 202.164.42.1, timeout is 2 seconds: .!!!!!!!!!!!!!!!!!!! Success rate is 95 percent (19/20), round-trip min/avg/max = 60/76/244 ms PC1#
Ping is successful, means NAT is working. Let’s have a look at NAT translations table on R1.
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 202.164.42.50:14 192.168.0.50:14 202.164.42.1:14 202.164.42.1:14
--- 202.164.42.50 192.168.0.50 --- ---
R1#
You can see that Inside local IP address 192.168.0.50 is translated to outside global 202.164.42.50 as we have configured.
Now if I remove the static NAT command from R1, you can see that translation will no longer be done and therefore PC1 can not ping R2.
R1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#no ip nat inside source static 192.168.0.50 202.164.42.50
R1(config)#^Z
R1#
*Jul 1 17:42:44.915: %SYS-5-CONFIG_I: Configured from console by console
R1#
PC1#ping 202.164.42.1 repeat 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 202.164.42.1, timeout is 2 seconds:
..........
Success rate is 0 percent (0/10)
PC1#
This concludes our simple Static NAT configuration.
Dynamic NAT Configuration
In Dynamic NAT, we have a pool of addresses which can be used to provide public or global IP addresses to a group of users on the inside network.
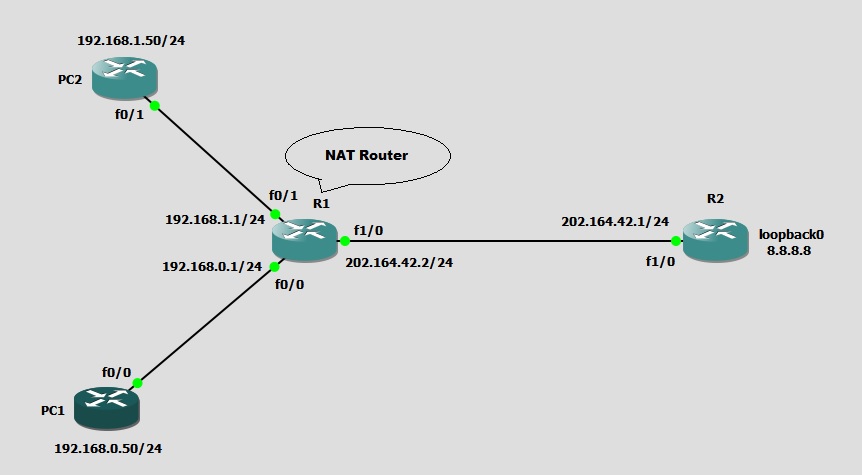
Below is the sample network I am going to use for configuring Dynamic NAT. We are simulating the internet using R2 loopback0 interface (8.8.8.8). PC1 and PC2 are simulating our LAN subnets, actually these are routers but I’ve disabled ip routing and configured ip default-gateway command so that these will act as end devices.
So, let’s get started.
Step:-1
Configure R1:
R1#config term R1(config)#int fa0/0 R1(config-if)#ip address 192.168.0.1 255.255.255.0 R1(config-if)#no shut R1(config-if)#ip nat inside R1(config)#int fa0/1 R1(config-if)#ip address 192.168.1.1 255.255.255.0 R1(config-if)#no shut R1(config-if)#ip nat inside R1(config-if)#int fa1/0 R1(config-if)#ip address 202.164.42.2 255.255.255.0 R1(config-if)#no shutdown R1(config-if)#ip nat outside R1(config-if)#exit R1(config)#ip route 0.0.0.0 0.0.0.0 202.164.42.1 R1(config)#end R1#
In above configuration steps, I configured IP addresses, defined inside and outside networks and finally added default route so that R1 can reach internet. The ip nat inside command declares the interface to be connected to inside network and ip nat outside declare the interface for outside network.
Remember we are simulating internet to be on R2 loopback0 interface with IP address 8.8.8.8 which is reachable via 202.164.42.1.
Configure R2:
R2#conf t Enter configuration commands, one per line. End with CNTL/Z. R2(config)#int fa1/0 R2(config-if)#ip address 202.164.42.1 255.255.255.0 R2(config-if)#no shut R2(config-if)#no shutdown R2(config-if)#int loop0 R2(config-if)#ip address 8.8.8.8 255.255.255.255 R2(config-if)#no shut R2(config-if)#exit R2(config)#ip route 0.0.0.0 0.0.0.0 202.164.42.2 R2(config)#^Z R2#
Similarly, I configured IP addresses on R2 and added a default route towards our LAN.
Configure PC1:
PC1#conf t Enter configuration commands, one per line. End with CNTL/Z. PC1(config)#int fa0/0 PC1(config-if)#ip address 192.168.0.50 255.255.255.0 PC1(config-if)#no shut PC1(config-if)#exit PC1(config)#no ip routing PC1(config)#ip default-gateway 192.168.0.1 PC1(config)#^Z PC1# *Jul 2 11:20:30.623: %SYS-5-CONFIG_I: Configured from console by console PC1#
The no ip routing command is used to disable ip routing on router and ip default-gateway command assigns default gateway. Now this router will act as end device (PC).
Configure PC2:
PC2#conf t Enter configuration commands, one per line. End with CNTL/Z. PC2(config)#int fa0/1 PC2(config-if)#ip address 192.168.1.50 255.255.255.0 PC2(config-if)#no shut PC2(config-if)#exit PC2(config)#no ip routing PC2(config)#ip default-gateway 192.168.1.1 PC2(config)#^Z PC2# *Jul 2 11:20:30.623: %SYS-5-CONFIG_I: Configured from console by console PC2#
At this point we have configured basic networking in our sample network but NAT is not configured yet. The following steps will be used to configure dynamic NAT on R2.
Step:-2
Create standard access-list to match the interesting traffic which will be allowed for NAT.
R1#config term R1(config)#access-list 1 permit 192.168.0.0 0.0.255.255 R1(config)#end R1# *Jul 2 11:35:12.939: %SYS-5-CONFIG_I: Configured from console by console R1#
I have created a standard access list 1 which will permit our source IP subnets 192.168.0.0 and 192.168.1.0.
Step:-3
Create the NAT pool of public IP addresses and configure NAT.
I have used 202.164.42.1 and 202.164.42.2 addresses from subnet 202.164.42.0/24. Since it provides us 254 valid hosts and only 2 are used, I can create the NAT pool using remaining addresses.
R1#config term R1(config)# R1(config)#ip nat pool techtutsonline 202.164.42.10 202.164.42.20 netmask 255.255.255.0 R1(config)#ip nat inside source list 1 pool techtutsonline R1(config)#end R1#
The ip nat pool techtutsonline 202.164.42.10 202.164.42.20 netmask 255.255.255.0 command created the NAT pool with the name techtutsonline with IPs starting from 202.164.42.10 to 202.164.42.20. The ip nat inside source list 1 pool techtutsonline will configure NAT to allow source IPs maching access-list 1 to be dynamically translated to public IP addresses from NAT pool.
Verify Dynamic NAT Process
We can verify the dynamic NAT by using show ip nat translations command on our NAT router. Let’s have a look.
R1#show ip nat translations R1#
There is nothing in NAT table yet but as soon as any user try to access internet, their private IP will be converted by using public IP out of pool. In order to simulate this, run a ping to 8.8.8.8 from PC1 and PC2.
PC1#ping 8.8.8.8 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 60/63/64 ms PC1#
PC2#ping 8.8.8.8 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 64/73/80 ms PC2#
Now let’s repeat show ip nat translations command on R1.
R1#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 202.164.42.10:1 192.168.0.50:1 8.8.8.8:1 8.8.8.8:1 --- 202.164.42.10 192.168.0.50 --- --- icmp 202.164.42.11:2 192.168.1.50:2 8.8.8.8:2 8.8.8.8:2 --- 202.164.42.11 192.168.1.50 --- --- R1#
Here you can see the private IP of PC1 and PC2 have been translated to 202.164.42.10 and 202.164.42.11 respectively.
This works on first come first serve basis. Remember one thing that the number of users who can simultaneously access the internet using dynamic NAT is equal to total number of IP addresses allocated in NAT pool because it does not use any ports. Dynamic NAT allocates one complete public IP for one private host inside your network.
For more information of NAT process, you can use show ip nat statistics command.
R1#show ip nat statistics
Total active translations: 2 (0 static, 2 dynamic; 0 extended)
Outside interfaces:
FastEthernet1/0
Inside interfaces:
FastEthernet0/0, FastEthernet0/1
Hits: 16 Misses: 2
CEF Translated packets: 18, CEF Punted packets: 0
Expired translations: 2
Dynamic mappings:
-- Inside Source
[Id: 1] access-list 1 pool techtutsonline refcount 2
pool techtutsonline: netmask 255.255.255.0
start 202.164.42.10 end 202.164.42.20
type generic, total addresses 11, allocated 2 (18%), misses 0
Queued Packets: 0
R1#
You can also see total addresses in NAT pool and currently allocated addresses etc. This command is helpful for detailed statistics.
This concludes our Dynamic NAT process.
Port Address Translation Configuration
Port Address Translation (PAT) also known as overloading is a type of NAT that translates inside local RFC1918 private addresses to a single inside globally unique (public). This is most widely used NAT technology in the world.
For demonstration of PAT, I will use the same network diagram which we used in Dynamic NAT.
So first of all I am going to remove NAT pool, access-list and actual NAT configuration command while leaving every other configuration same.
R1#conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)#no ip nat inside source list 1 pool techtutsonline R1(config)#no ip nat pool techtutsonline 202.164.42.10 202.164.42.20 netmask 255.255.255.0 Dynamic mapping in use, do you want to delete all entries? [no]: no access-list 1 permit 192.168.0.0 0.0.255.255 % Please answer 'yes' or 'no'. Dynamic mapping in use, do you want to delete all entries? [no]: y R1(config)# R1(config)#no access-list 1 permit 192.168.0.0 0.0.255.255 R1(config)#end
I have only removed NAT pool, access-list and actual NAT configuration command from router R1 since everything in network is same. If you are configuring PAT from scratch, you can see Dynamic NAT configuration to assign IP address and configure interfaces as inside and outside.
Configuration Steps:
Create Access-List
First of all we need to create access-list to match interesting traffic. This time I am going to use extended named access-list. But you can also use standard access-list as we did in dynamic NAT.
R1#config t Enter configuration commands, one per line. End with CNTL/Z. R1(config)# R1(config)#ip access-list extended PAT-ACL R1(config-ext-nacl)#permit ip 192.168.0.0 0.0.255.255 any R1(config-ext-nacl)#exit R1(config)#
I created the named access-list PAT-ACL which will allow every ip traffic from our inside network hosts.
Configure PAT
R1(config)#
R1(config)#ip nat inside source list PAT-ACL interface fastEthernet 1/0 overload
R1(config)#end
R1#
*Jul 2 14:13:32.399: %SYS-5-CONFIG_I: Configured from console by console
R1#show ip nat translations
R1#
The ip nat inside source list PAT-ACL interface fastEthernet 1/0 overload command is doing the real magic of translating multiple inside local addresses to a single inside global address. You can see that router does not show any translations yet.
Now go to PC1 and PC2 and run ping to 8.8.8.8 and then come back again on R1 to examine the translations. You will see something as below
R1#show ip nat translations Pro Inside global Inside local Outside local Outside global icmp 202.164.42.2:1 192.168.0.50:1 8.8.8.8:1 8.8.8.8:1 icmp 202.164.42.2:0 192.168.1.50:0 8.8.8.8:0 8.8.8.8:0 R1#
You can see that both of hosts 192.168.0.50 and 192.168.1.50 are mapped to single public IP which is configured on outside interface but this time a port number is allocated to each session going out and coming back in.
For further details, show ip nat statistics command can be used.
R1#show ip nat statistics Total active translations: 1 (0 static, 1 dynamic; 1 extended) Outside interfaces: FastEthernet1/0 Inside interfaces: FastEthernet0/0, FastEthernet0/1 Hits: 234 Misses: 4 CEF Translated packets: 237, CEF Punted packets: 0 Expired translations: 4 Dynamic mappings: -- Inside Source [Id: 2] access-list PAT-ACL interface FastEthernet1/0 refcount 1 Queued Packets: 0 R1#
If you are doing this configuration in test lab, I would recommend using debug ip nat command on NAT router, which will tell you the status of translations in real-time. but if you are configuring this on production router, it is not recommended to use debug command.
R1#debug ip nat
IP NAT debugging is on
R1#
*Jul 2 14:30:55.483: NAT*: s=192.168.0.50->202.164.42.2, d=8.8.8.8 [115]
*Jul 2 14:30:55.519: NAT*: s=8.8.8.8, d=202.164.42.2->192.168.0.50 [115]
*Jul 2 14:30:55.567: NAT*: s=192.168.0.50->202.164.42.2, d=8.8.8.8 [116]
*Jul 2 14:30:55.627: NAT*: s=8.8.8.8, d=202.164.42.2->192.168.0.50 [116]
*Jul 2 14:30:55.691: NAT*: s=192.168.0.50->202.164.42.2, d=8.8.8.8 [117]
*Jul 2 14:30:55.755: NAT*: s=8.8.8.8, d=202.164.42.2->192.168.0.50 [117]
*Jul 2 14:30:55.815: NAT*: s=192.168.0.50->202.164.42.2, d=8.8.8.8 [118]
*Jul 2 14:30:55.879: NAT*: s=8.8.8.8, d=202.164.42.2->192.168.0.50 [118]
*Jul 2 14:30:55.927: NAT*: s=192.168.0.50->202.164.42.2, d=8.8.8.8 [119]
R1#
*Jul 2 14:30:55.995: NAT*: s=8.8.8.8, d=202.164.42.2->192.168.0.50 [119]
R1#
After running debug ip nat command on R1, I fired ping from PC1 to destination:8.8.8.8 and you can see the translation occurring in real-time.
This concludes the configuration of PAT or overloading.